WALLIX PAM Partner

Secure Your Digital Future with CLI Secure and WALLIX
At CLI Secure, we are proud to partner with WALLIX, the global leader in access and digital identity security. This partnership enables us to offer advanced solutions in Privileged Access Management (PAM) that are at the forefront of protecting IT networks and critical data against the ever-evolving landscape of cyber threats.
WALLIX’s cutting-edge technology helps safeguard your organization’s digital assets by enhancing detection capabilities and resilience against cyberattacks. Our collaborative efforts focus on maintaining the continuity of IT systems across various platforms, including cloud environments and industrial networks.
Together, CLI Secure and WALLIX deliver security solutions that are not only robust but also tailor-made to meet the unique needs of your business. By simplifying compliance with regulatory requirements, we ensure that accessing your critical IT infrastructure and safeguarding sensitive data is seamless and secure.

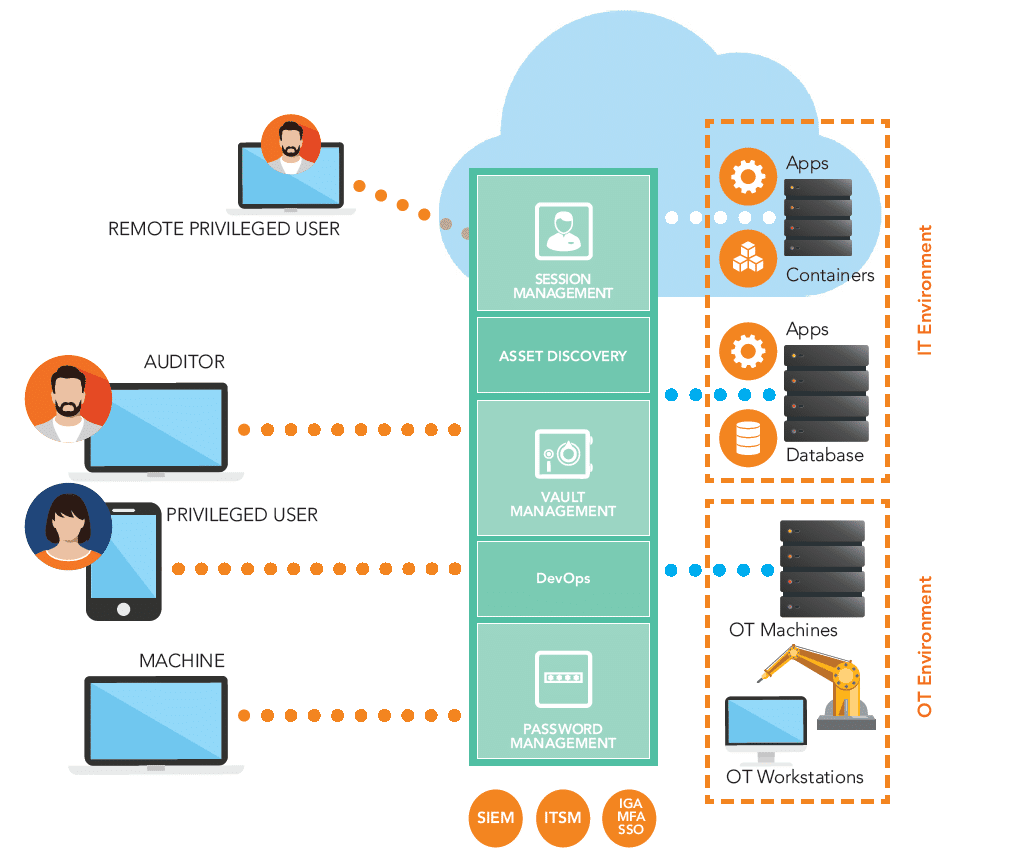
Privileged Access Management with Wallix PAM
Centralized Control and Monitoring of Privileged Access to Sensitive Assets
At CLI Secure, alongside our partnership with Wallix, we recognize the critical role that Privileged Access Management (PAM) plays in mitigating cyber-attacks. Hackers commonly exploit privileged accounts to breach and navigate through organizations.
Wallix PAM stands as a premier PAM solution that provides strong security and control over privileged access to essential IT infrastructure. As an agentless solution, Wallix PAM allows for effortless deployment across on-premise, private, and public cloud environments.
Additionally, Wallix PAM is offered as a Service, presenting a more economical and less resource-demanding alternative. This partnership enhances our ability to secure your digital assets effectively.
Secure. Comply. Enable.
Manage complexity and mitigate risk.

Enhanced Security
At CLI Secure, in collaboration with Wallix, we emphasize the importance of Privileged Access Management (PAM) in reducing the risk of unauthorized access to sensitive systems and data. PAM effectively manages, monitors, and controls privileged accounts, implementing the principle of least privilege. This ensures that users are granted access only to the resources essential for their specific roles. Our partnership with Wallix enhances our capability to safeguard your critical digital infrastructure by tightly regulating access permissions.

Reduced Attack Surface
At CLI Secure, together with Wallix, we focus on minimizing potential cyber threats and insider attacks by restricting access rights and credentials through Privileged Access Management (PAM). This approach effectively reduces the attack surface by ensuring that privileged accounts are tightly controlled. Our collaboration with Wallix strengthens our commitment to providing robust security measures that protect your organization from unauthorized access and breaches.

Credential Management
At CLI Secure, in partnership with Wallix, we highlight the value of Privileged Access Management (PAM) tools in centralizing the management of privileged account credentials. These tools ensure the use of strong, frequently updated passwords or alternative authentication methods such as SSH keys. This central management significantly lowers the risk of credential theft and misuse, reinforcing our joint efforts to enhance your organization’s security posture.

Privilege Elevation and Session Isolation
At CLI Secure, along with our partner Wallix, we emphasize the critical functionality of Privileged Access Management (PAM) in enabling controlled privilege elevation processes. PAM ensures that temporary access to sensitive resources is granted only when necessary. Additionally, session isolation is utilized to restrict access to specific resources, effectively preventing lateral movement within a network. Our partnership with Wallix plays a vital role in securing and managing access within your organization’s IT environment.
Features
Reduce the Attack Surface
- Discover assets automatically
and remove all local privileged
accounts - Set up authorization rules to
supervise critical systems
access - Use the least required privilege
to perform tasks - Attribute privileges “Just in
Time” for authorized users
Control Sessions
- Monitor sessions in real time
with Session Sharing - Record all sessions and
extract related metadata for
analysis - Raise alarms after malicious
activity detection and
terminate sessions
Manage Secrets
- Store secrets of human and
non-human users securely - Update passwords with
automated rotation based on
time and/or usage - Remove passwords from disks
Audit Activity
- Manage KPIs with reports
and dashboards - Correlate suspicious behavior
with SIEM integration - Deploy quickly with no
interruption to daily workflows
